Cracking Linux passwords is essentially the same as cracking Windows passwords in the sense that you start by getting the hashes and then you try to find the matching passwords.
But, being completely different operating systems, the tools and procedures also have to be distinct.
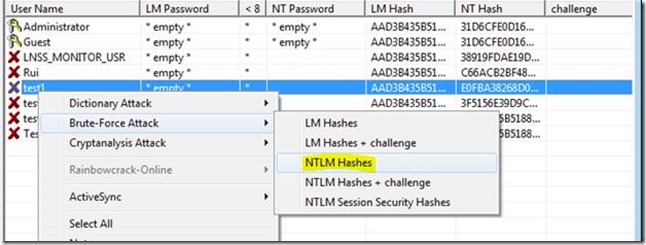
Create test users
sudo adduser [username]
Create users with these passwords:
test1 abc
test2 abcde
test3 password
test4 Alcanena
test5 Pa$$w0rd
Install John the Ripper Password Cracking Tool
John the Ripper is not installed by default in most Linux distros. If you are using Debian/Ubuntu Linux, enter:
sudo apt-get install john
In CentOS, Fedora or Redhat Linux, just use the appropriate package manager
sudo dnf install john
or
sudo yum install john
Unshadow the passwords
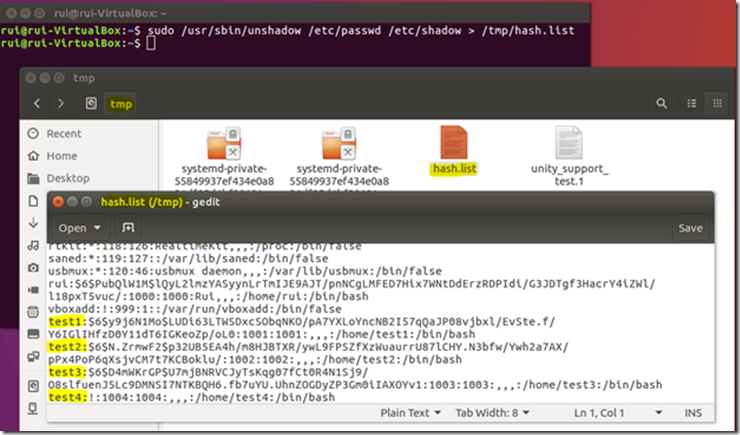
Generally, all modern Linux operating systems use some sort of the shadow password suite, where the file /etc/passwd has asterisks or other symbol instead of passwords hashes, and the hashes are in the /etc/shadow file which is readable by the superuser only.
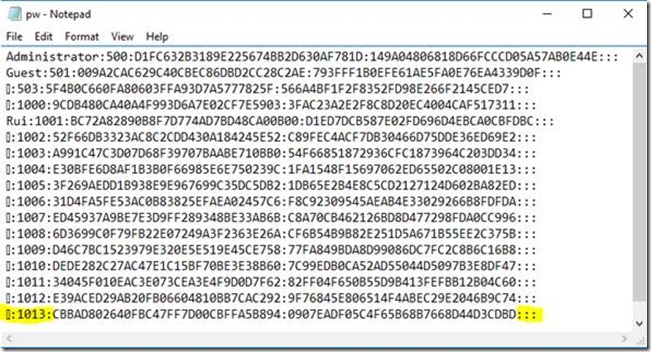
This is a passwd file:
The /etc/shadow file stores actual password hashes for each user’s account with additional properties related to user password i.e. it stores secure user account information. All fields are separated by a colon (:) symbol and it contains one entry per line for each user listed in /etc/passwd file:
First use the unshadow command to combine the /etc/passwd and the /etc/shadow files so John can use them properly. You can attack the shadow file directly but then you won’t be able to take full advantage of John capabilities.
NOTE: The unshadow application is distributed with John the Ripper software
On a normal system, you’ll need to run unshadow as root to be able to read the shadow file.
On Ubuntu type:
sudo /usr/sbin/unshadow /etc/passwd /etc/shadow > /tmp/hash.list
On CentOS / Fedora Linux type:
/usr/bin/unshadow /etc/passwd /etc/shadow > /tmp/hash.list
Now it might be a good idea to create a copy of your hashes just in case you want to use them in some other experimenting.
cp /tmp/hash.list /tmp/hash.list.original
Use John to crack passwords
John the Ripper can work in the following modes:
- Wordlist: John will simply use a file with a list of words to launch a dictionary attack.
- Single crack: In this mode, john will try to crack the password using the login/GECOS information as passwords.
- Incremental: This is the mode where John launches a brute force attack.
To use John, you just need to supply it a file created using unshadow command along with desired options. If no mode is specified, john will try “single” first, then “wordlist” and finally “incremental” password cracking methods.
Using John in single mode
Just type:
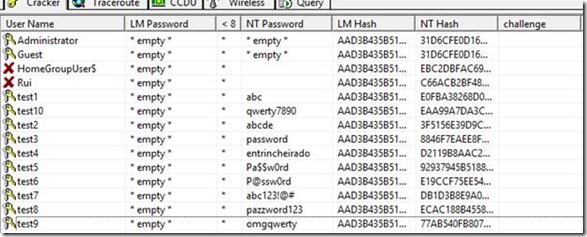
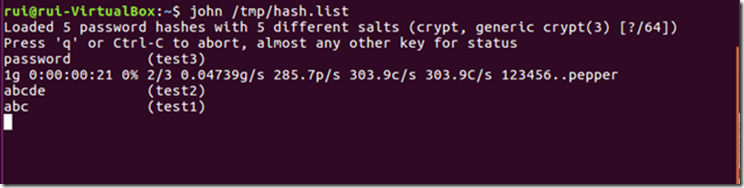
john /tmp/hash.list
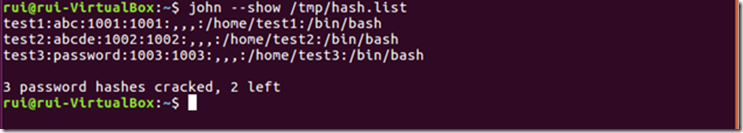
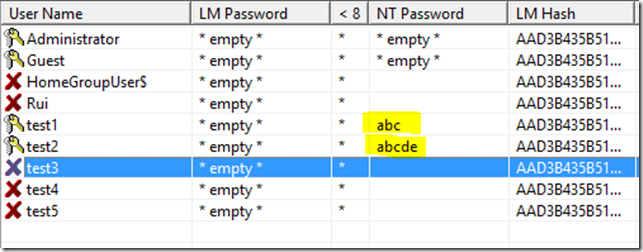
In less than a minute, the first three passwords are cracked. Then it’s better to interrupt the processing because it might take forever…
To see the cracked passwords, enter:
john --show /tmp/hash.list
Using John in wordlist mode
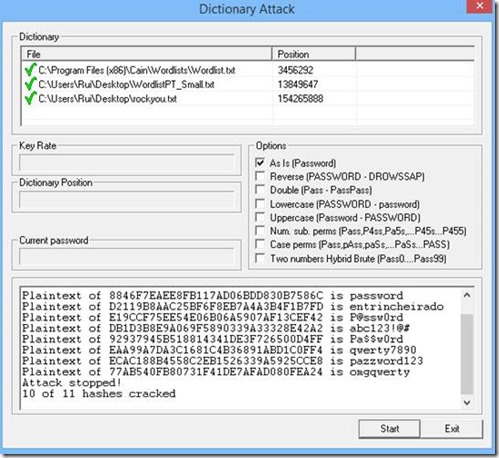
When I showed you how to crack Windows passwords, I demonstrated the effectiveness of using a good wordlist. John comes with a small wordlist and you can try to use it just to see what happens.
Start by replacing the original hash.list file, using the copy you made previously
cp /tmp/hash.list.original /tmp/hash.list
To force John to crack those same hashes again, you have to remove the john.pot file.
rm ~/.john/john.pot
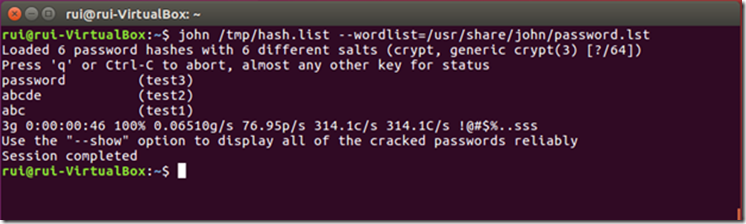
Start John in wordlist mode using the proper parameter:
john /tmp/hash.list --wordlist=/usr/share/john/password.lst
Not bad, however it’s highly recommended that you obtain a larger wordlist. But first, create a proper place to place it:
sudo mkdir /usr/share/john/wordlists
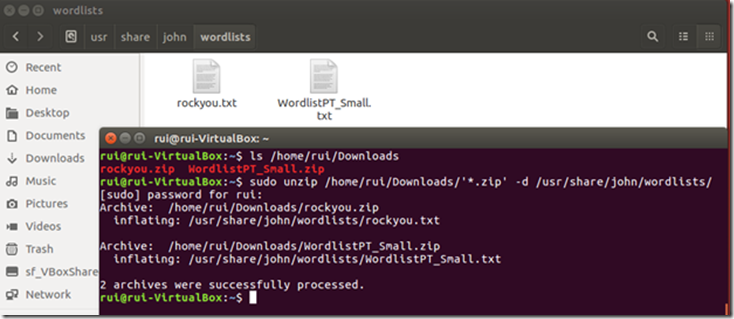
Use your browser and go to http://bit.do/Word_Lists. Download the two files and extract them to the directory you’ve just created.
To save the files:
To extract them:
sudo unzip /home/rui/Downloads/'*.zip' -d /usr/share/john/wordlists/
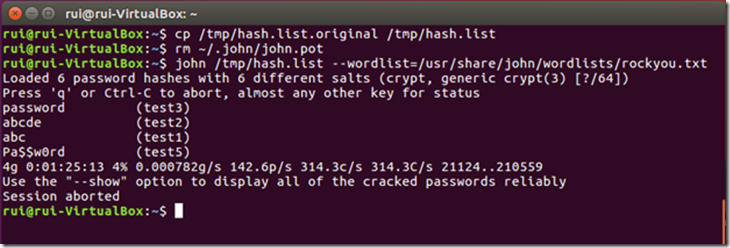
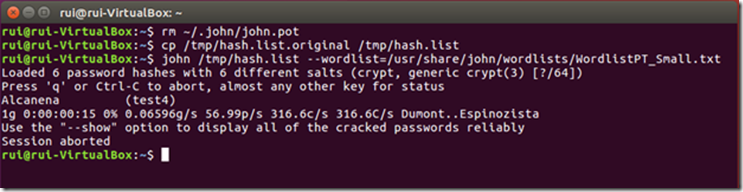
Replace the hash.list file and delete the john.pot file again. Repeat the attack using the rockyou.txt file as a wordlist.
I interrupted the procedure, but you can see that even after a long time it won’t crack test4’s password because it’s a Portuguese word and you won’t find it in any English wordlist.
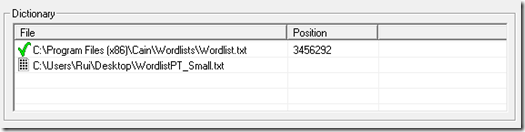
Repeat all the above procedures to launch an attack using the other wordlist:
Now John only found test4’s password because that’s the only word it could find in the used wordlist. So why don’t we use more than one wordlist?
Using John with multiple wordlists
By default, John the Ripper will use only one wordlist at a time. However, you can use it with multiple wordlists, combined or sequentially. If you want to combine all your wordlists into a single file and feed it into John:
cat /usr/share/john/wordlists/* | john …
Or you can use your wordlists one after another:
ls /usr/share/john/wordlists | xargs -t -I files john /tmp/hash.list --wordlist=/usr/share/john/wordlists/files
This command will list the ‘wordlists’ directory, pipe it to xargs, which will then create the command for each iteration. Then it’s just the standard John arguments.
Using John with Rules
Rule sets are defined in the john.conf file (usually found in /etc/john.conf) and are prefixed with a name so that you can specify them.
They look something like this:
Rules will tell John how to generate words to try, based on the words already present on your wordlist. Examples:
- john password_hashes.txt -w=password.lst --rules=single
- john password_hashes.txt -w=password.lst --rules=jumbo
- john password_hashes.txt -w=password.lst --rules=wordlist
Final note: John the Ripper is a great tool but it can be easily defeated if you follow my advices to create strong passwords. If you do, any attack will take a very long time to succeed… if ever!
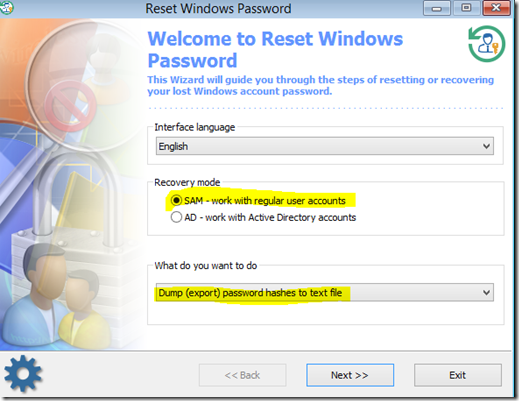
Previous post: Cracking Windows 10 Passwords





















![clip_image026[1] clip_image026[1]](https://lh3.googleusercontent.com/-TYDgC72Hr3g/WJ4GIKy_zLI/AAAAAAAAMzQ/VKD7E4Q0pL4/clip_image026%25255B1%25255D_thumb%25255B2%25255D.png?imgmax=800)