Creating the passwords
Time to continue our tour on the basic Windows cracking techniques. Let´s repeat the initial procedures explained in the previous post, but this time under Windows 10. Start by creating a few accounts and please use the exact same passwords:
net user test1 9#Yo~3 /add
net user test2 [1aZ4~ /add
net user test3 õç2}5$ /add
net user test4 7%hª5b /add
net user test5 9Ayo7Bz /add
net user test6 G85pdDL /add
net user test7 Ã49ÇaõF /add
net user test8 3É6Óêph /add
net user test9 3b567gh0 /add
net user test10 77xpy6vh /add
net user test11 4ã8ç6ê7õ /add
net user test12 56é2à4óç /add
Install CAIN and Win10Pcap (http://www.win10pcap.org/download/)
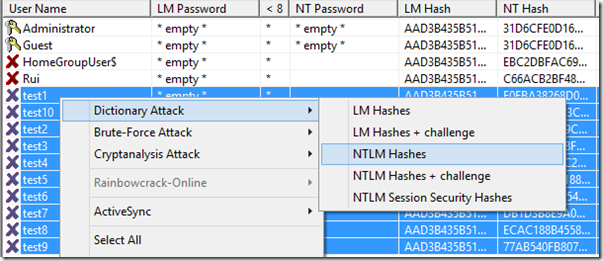
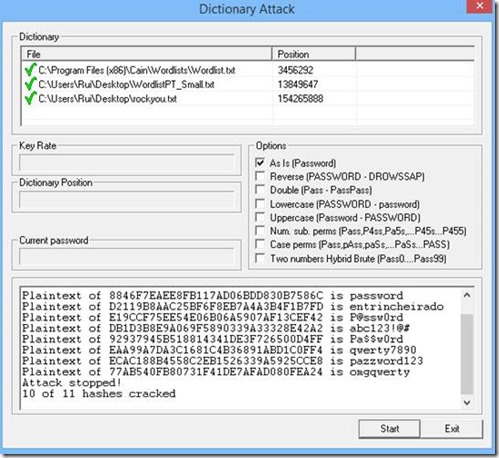
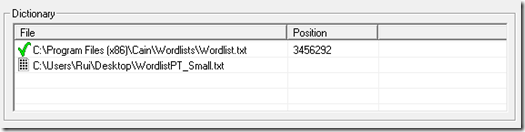
Try the dictionary attack using all three wordlist files previously used
No luck? Try Ophcrack.
The Live CD is unable to load the Windows 10 hashes!
Solution? Dump the hashes using another program.
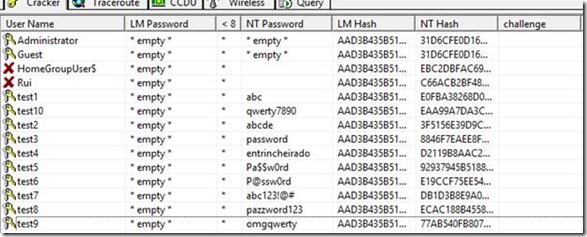
Dumping the hashes
CAIN can do it but it’s not the best solution because it only exports the hashes in LophtCrack format and Ophcrack will only read PwDump format hashes.
Windows 10 requires the use of the latest in password dumping technology, Pwdump v7.1. The main difference between pwdump7 and other pwdump tools is that this tool runs by extracting the binary SAM and SYSTEM file from the Windows filesystem and then the hashes are extracted.
Visit http://www.tarasco.org/security/pwdump_7/ and download the tool’s latest version.
Note: This tool can only be used against SAM and SYSTEM local files. Active directory passwords are stored in the ntds.dit file and that requires a completely different approach
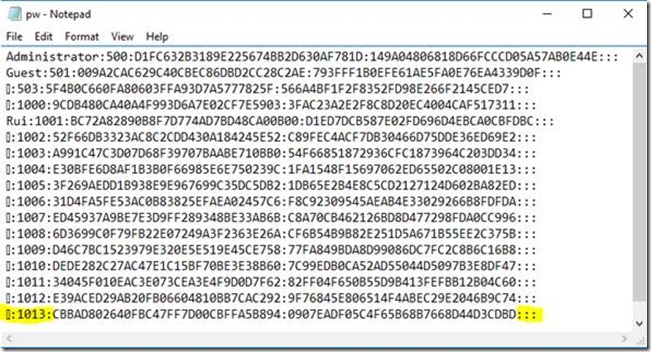
Running pwdump 7.1 in the latest Windows 10, fully updated, produces a file with some noticeable features:
No user names are displayed! The hashes are usable by Ophcrack but without the matching username they are almost useless.
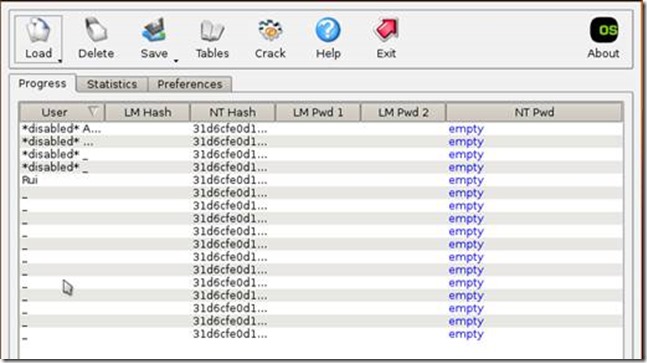
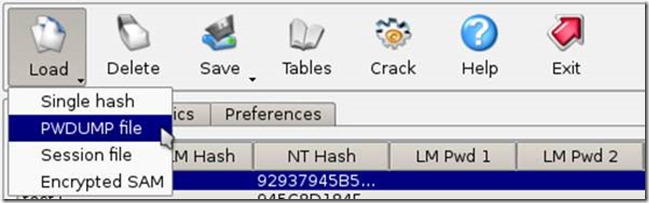
We need another tool to dump Windows 10 hashes, properly formatted for Ophcrack.
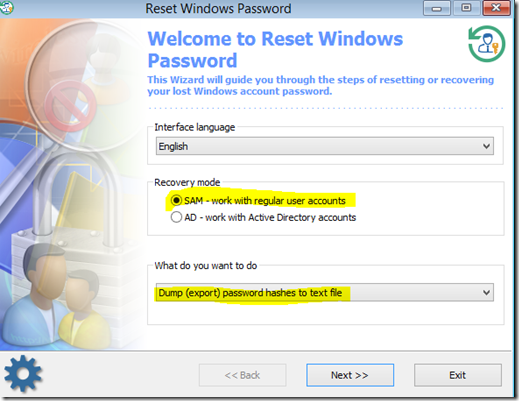
Get the ISO file for Reset Windows Password from the website:
http://www.passcape.com/reset_windows_password
Boot from the ISO and select the appropriate settings
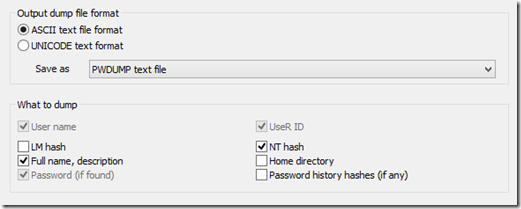
Select the appropriate path for the SAM and SYSTEM files
Choose the proper format for your output file
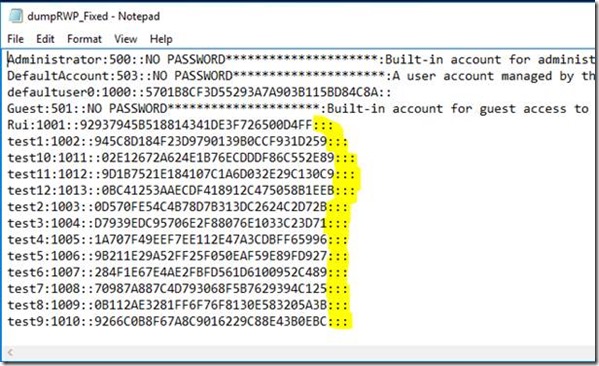
This is the result:
But this is not exactly the proper PwDump format ![]()
We still need to fix it:
This text file will be properly loaded by Ophcrack
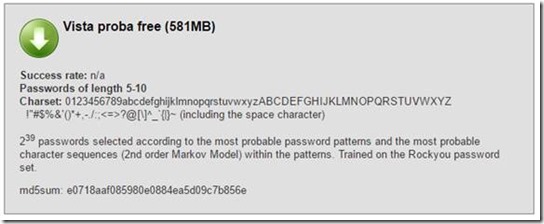
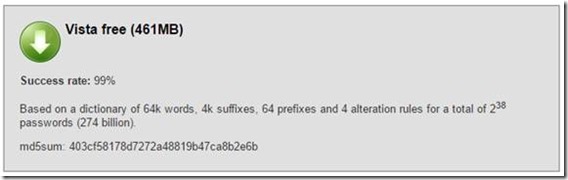
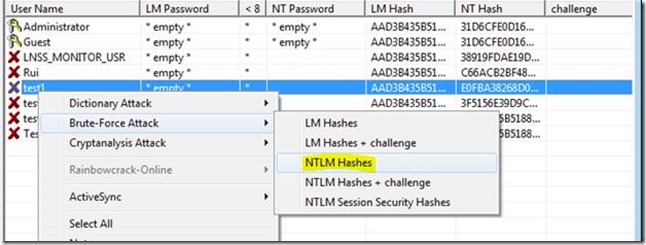
Time to crack these hashes using a much bigger set of rainbow tables; the 8 Gb Vista Special.
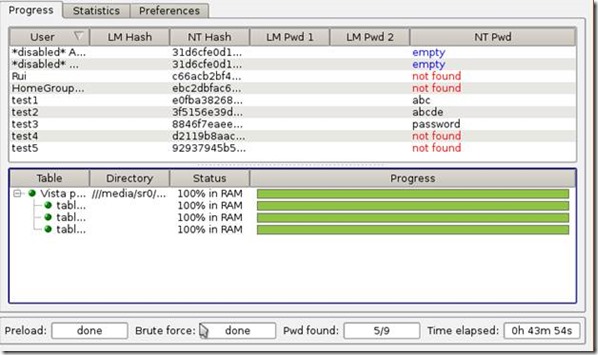
After more than one hour…
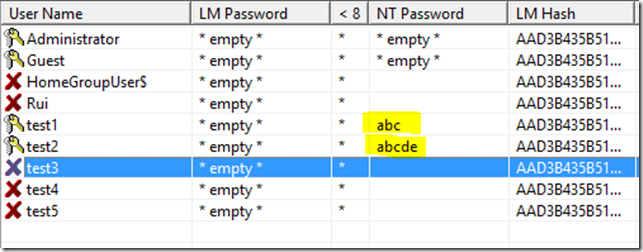
Conclusion:
Can you see the pattern?
The passwords I used were created taking into account the advertised success rate of the 8 Gb Vista Special rainbow tables. 99%… right?
However, only half of them were cracked! Why?
Because I used characters outside of the standard ASCII set. Namely, a number of characters widely used in my native language (Portuguese) like õ, ç, Ã or ê. These characters were not used in the generation of the rainbow tables and are also not normally used by the standard cracking tools, either to brute force or to play with the dictionary contents.
Therefore, even short passwords containing these characters are harder to crack than longer but stupid passwords. And that means you’ll be safer even against an attack done with the huge, sold rainbow tables because these are not generated to cover all possible characters. Go the Ophcrack’s website, notice the size of the existing tables and try to guess how big should a table be to cover all possible combinations for 10 characters using the extended ASCII set.
The same thing goes for the vast majority of the wordlist you’ll and find or even generate! And most cracking tools are programmed to perform only combinations within the standard ASCII set. It is possible to go beyond that, but it would make any attack extremely slow!
That are other many other tools available, some are better others are not, But the fact remains: Knowing the basic attack procedures will help you creating safer, better passwords by using proper characters and the right amount.
Password Security Tips
- Create passwords at least 10 characters long;
- Add complexity by using not only numbers and special characters but also by using extended ASCII characters like ê, ç, ò, ž, ä, etc;
- Use a password manager to help you generate and store your passwords;
- Use multifactor authentication.
Stay safe!
Previous post: Cracking Windows passwords
Next post: Cracking Linux passwords
















![clip_image026[1] clip_image026[1]](https://lh3.googleusercontent.com/-TYDgC72Hr3g/WJ4GIKy_zLI/AAAAAAAAMzQ/VKD7E4Q0pL4/clip_image026%25255B1%25255D_thumb%25255B2%25255D.png?imgmax=800)